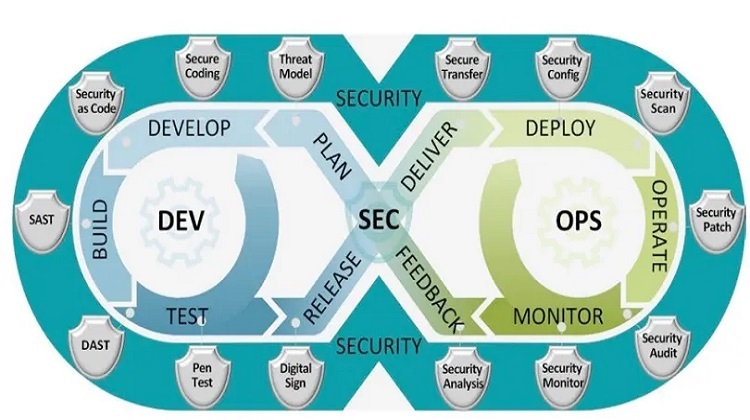
A lot of people may be wondering what the technology of DevSecOps is all about. One thing is for sure it has gone on to become a critical component of the software development process. Their main aim is to focus on securing applications and integrating security in the DevSecOps process. It is of help to audit the existing IT infrastructure; the security tools are updated in the pipeline and ensure better communication along with coordination between the various teams in an organization.
In simple terms, DevSecOps is a set of procedures, that go on to automate the build, and test along with the delivery process that making the process faster and more reliable. The process is automated between the IT and development teams. It goes on to promote security engagement as an active or major aspect of software development.
More about DevSecOps
This is a form of approach that provides security to applications or infrastructure based on DevOps methodology. It goes on to ensure that the application is less vulnerable to the end of the users. Everything is automated, from the process of security checks at the beginning of the application guidelines. Though the selection of tools is something that may not be enough security teams with the right set of tools may be needed to comply with the security needs.
Why DevSecOps is important?
Of late the intensity of cyber-attacks has increased manifold and even the most popular of organizations cannot deny the possibility of a cyber-attack. It has emerged in the last few years that zero attacks have gone on to compromise 65 % of total attacks or even the threat to a cloud-based application has increased manifold. These were considered to be negligible and organizations are shifting towards a cloud environment.
Incorporating security is vital to the DevSecOps process as security is something that cannot be neglected or underestimated. Due to the increased level of threat, it has given rise to the emergence of DevSecOps
The benefits of adopting security in DevSecOps
Some of the benefits of DevSecOps are as follows
- Delivery rate increases and expenses reduce
- Monitoring, security, deployment checks and notifying systems right from the starting stage.
- Right from the primitive stages of development it embraces, openness and transparency
- Is secured by design and ability to measure
- In case of a security incident faster pace of recovery
- Overall levels of security improvements, by contributing to the immutable infrastructure that leads to an improvement in security automation
The features of DevSecOps security
DevSecOps along with the tools of DevSecOps main aim is to integrating standards and security principles in the DevSecOps cycle. Their main aim is to implement security control at each level of the DevSecOps levels. Hence it paves way for an effective level of communication between the release engineers and security teams.
- In applications vulnerabilities are reduced
- Implementation of compliance into the delivery pipeline from day one.
- Maintaining along with ensuring compliance
- An ability to respond to changes in a rapid manner
- More security along with agility is provided to the security teams
- A trustful relationship with the organizations is developed.
Why DevSecOps tend to matter?
During a joint venture, the operation and development of the DevSecOps teams is important and a few reasons are mentioned below
- A focus on the security of the application from the starting stages
- It enables to provide better results.
The benefits of DevSecOps from an organizational point of view
Just as is the case with any low-level technology automation practice, repetitive tasks can be automated. It goes on to include the monitoring and automation of the security features with an application. It enables better monitoring of the apps from a cyber-attack point of view.
Speed is of the essence in the software development cycle, but it comes at the loss of code accuracy. In the frameworks, it is essential to implement, automated code verification modules. They can detect the errors and figure out the remedial measures that is not going to slow down the software updates or the deployment schedules.
It needs to include processes, that are bound to automatically integrate the security functions across the software in a uniform manner. Such a structured approach goes on to develop a consistent security foundation where security is formulated in the same manner an application is moving through the life cycle process.
Advancement of the frameworks would point to cashing in on the benefits of machine learning and AI to streamline and fine-tune complex tasks. Appealing suggests a couple of examples
- The collection along with analysing the software with operating system logging information. This gives an idea about the bad actors that are planning to breach a target. It is based on this information that AI can suggest code alterations or structural changes identify code vulnerabilities in a proactive manner.
- It is from a coding point of view, that the changes can run through finely tuned modules on how a particular change may have an impact on the other aspects of an application.
Since the tools along with the process of DevSecOps are tuned and developed it would make less sense to manually replicate them where complete resources need to be formulated. In some cases, the entire framework has to be placed in physical locations. If you need to scale up and down the process within a month’s notice the process needs to be fully automated DevSecOps best practices. It was stated that the number of security incidents at the workplace reduced drastically.
For any business vertical adhering to industry and business policies is mandatory. There is a need to audit and report functions as it needs to identify relevant information and the data is to be displayed in an understandable and consistent manner. For a lot of security teams reporting along with auditing may turn out be a tedious task and hence they need to identify relevant information. There are bound to be complications with the ever change trends of data or due to lack of visbility.